Windows 8 introduces a new security feature?called Secure Boot,?which protects the Windows boot configuration and components, and loads an Early Launch Anti-malware (ELAM) driver. This driver starts before other boot-start drivers and enables the evaluation of those drivers and helps the Windows kernel decide whether they should be initialized. By being launched first by the kernel, ELAM is ensured that it is launched before any other third-party software. It is therefore able to detect malware in the boot process itself and prevent it from loading or initializing.
Windows Defender takes advantage of Early-Launch Anti-Malware and you therefore see that it no longer loads after the start-up process is complete, but early on during boot process.
Third-party antivirus software too are able to take advantage of the ELAM technology. To do so, they will have to integrate the same Early Launch Anti-Malware (ELAM) capability in their own software. To help security software vendors get started, Microsoft has released a whitepaper?that provides information about developing Early Launch Anti-Malware (ELAM) drivers for Windows operating systems. It provides guidelines for anti-malware developers to develop anti-malware drivers that are initialized before other boot-start drivers, and ensure that those subsequent drivers do not contain malware. Several antivirus companies, who have released their updated solutions for Windows 8 already incorporate this technology.
The Early Launch Antimalware boot-start driver has classified the drivers as follows:
- Good: The driver has been signed and has not been tampered with.
- Bad: The driver has been identified as malware. It is recommended that you do not allow known bad drivers to be initialized.
- Bad, but required for boot: The driver has been identified as malware, but the computer cannot successfully boot without loading this driver.
- Unknown: This driver has not been attested to by your malware detection application and has not been classified by the Early Launch Antimalware boot-start driver.
By default, Windows 8 loads those drivers which have been classified as Good, Unknown and Bad but Boot Critical; ie 1, 3 and 4 above. Bad drivers are not loaded.
While this setting is best left at its default value, if you wish, you can change this setting via your Group Policy Editor. To do so, open the WinX menu > Run > gpedit.msc > Hit Enter. Navigate to the following policy setting:
Computer Configuration > Administrative Templates >? System > Early Launch Antimalware
In the right pane, double-click on? Boot-Start Driver Initialization Policy to configure it.
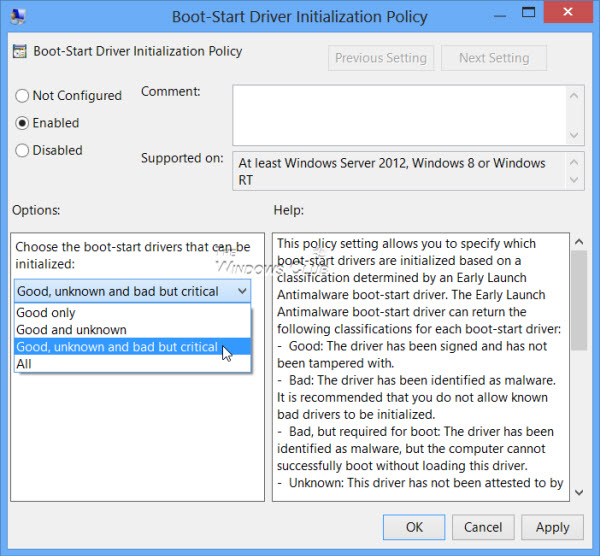
You will see the default configuration of Not Configured. If you disable or do not configure this policy setting, the boot start drivers determined to be Good, Unknown or Bad but Boot Critical are initialized and the initialization of drivers determined to be Bad is skipped.
If you Enable this policy setting you will be able to choose which boot-start drivers to initialize the next time the computer is started.
If you are using Windows 8, you want to check if your anti-malware software includes an Early Launch Antimalware boot-start driver. If it doesn?t, all boot-start drivers will be? initialized, and you will not be able to take advantage of this new ELAM technology.?
If you have liked this post, you might want to check out some more, on topics like Features, Security, Windows 8.
john elway john elway i have a dream speech fox news debate martin luther king jr mlk mlk
No comments:
Post a Comment